Visit the Psycho Cod3r network for great tutorials, projects, and rambles on all things tech! Check out my blog articles and read about Linux, Unix, cyber-security, retrocomputing, data science, and more!

Disclaimer: Don’t be a dumbass. Follow Norman Bates’ advice at your own risk.
Hello, and welcome to my WordPress site. I’m Michael Warren, a tech-savvy psycho who likes to do hacky stuff and tinker with technology. I have a ton of interesting stuff on this site, so feel free to look around. Follow me if you like what you see. 😛
Hot Topics:

Here are some of my top subjects that I write on, so look through the list below to see if you find anything that interests you:
Languages:
C
QBASIC
Unix shell scripting
R
Other topics:
Algorithms
Reverse engineering
Data science
Unix and Linux
Vim
Ethical hacking
MS-DOS
VirtualBox
Hex editor hacking
Apple sux!
Latest Updates by Category:
Data Science:
Analyzing Twitter Analytics Data in R
I’ve spent a lot of time trying to figure out how to become popular on Twitter. It’s pretty much impossible if you’re not already a celebrity or public figure, but I figured I’d try to maximize my success anyway. I did some data analysis using CSV data that I exported from the Twitter Analytics page. Analytics is a lesser-known feature of Twitter that is (as far as I can tell) only available on…
Continue Reading
More Articles →
Security and Privacy:
Before You Start Using a VPN, Read This
Use of VPNs has exploded in the last few years, pushed by increasing awareness of privacy issues among citizens as well as governments and corporations doubling down on their censorship and surveillance efforts. Now that we have AI capable of building frighteningly accurate psychological profiles of people based on their browsing habits, using a VPN or other privacy-enabling technology is more important than ever. But simply using a VPN, by itself, does not ensure privacy. There are a few…
Continue Reading
More Articles →
Unix and Linux:
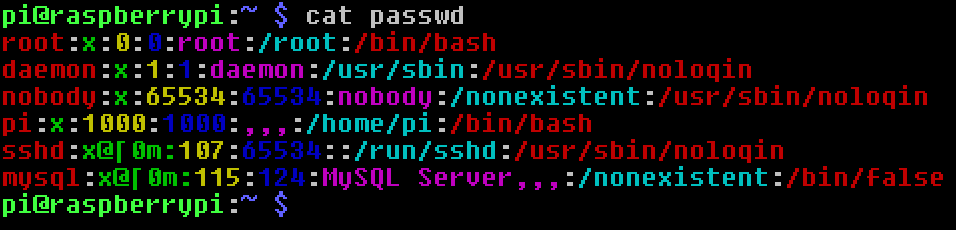
Making Text Files Colorful – With a Hex Editor
Hello, friends. In this tutorial I will be sharing a neat hack that you can use to add colors and other styles to a plain text file. This means that when you view the file with cat, the text will be color-coded. We accomplish this using…
Continue Reading
More Articles →
Retrocomputing:
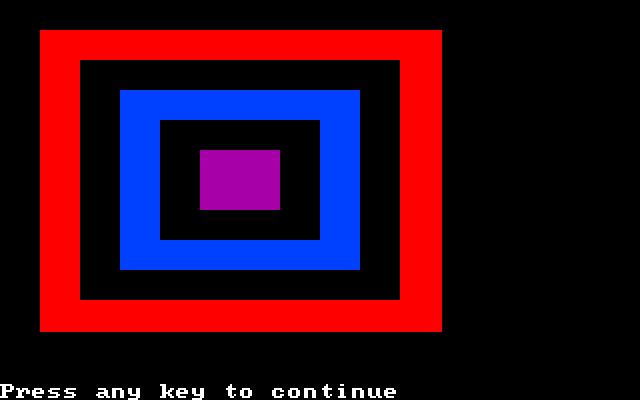
Computer Graphics in DOS
We know DOS primarily as a text-mode operating system. You turn on your DOS VM and it logs you into a command prompt. But DOS also allows for some pretty neat 8-bit graphics, which can add flavor to the sometimes dry and boring CLI. In this article I will be exploring the many aspects of computer graphics in the DOS world….
Continue Reading
More Articles →
C Programming:
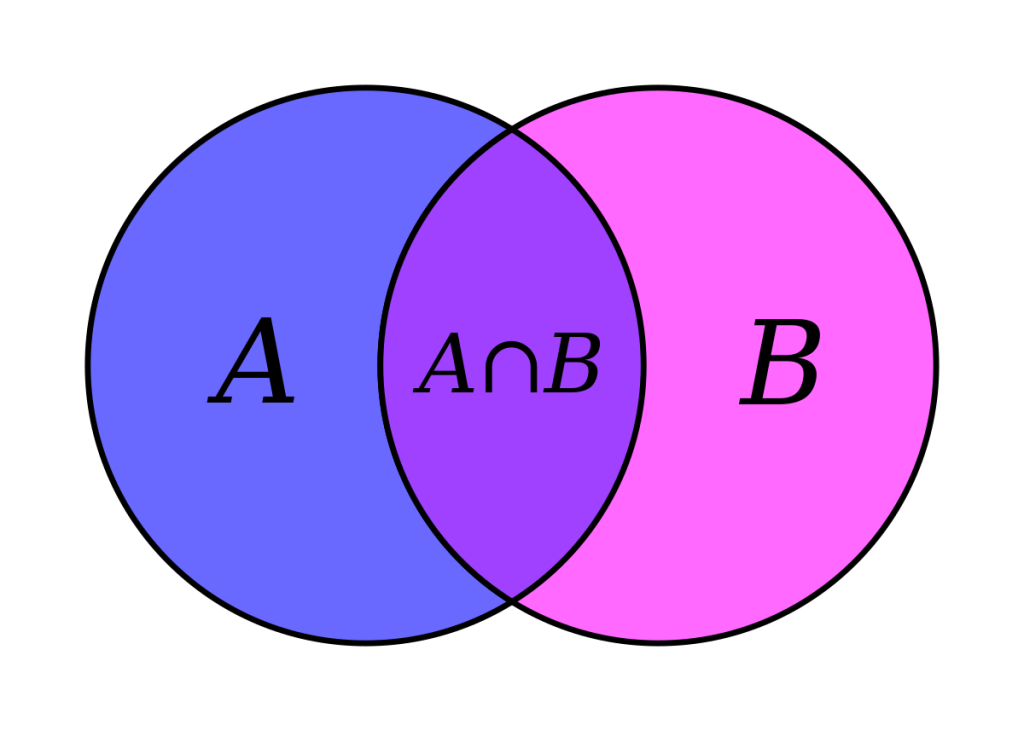
Adding Set Types to the C Programming Language
This is my third article about creating user-defined data types in C. The other two were mainly concerned with implementing numeric types to get better precision. In this one we will be implementing a completely new (non-numeric) data type based on the set concept from set theory. Set types are a feature in some programming languages, most notably the…
Continue Reading
More Articles →
Hacking:
Shell Script for Launching a Local Denial-of-Service Attack
Haven’t written anything about either pen-testing or Linux shell scriptin
recently, so I thought I’d share a neat script I wrote several years ago that I used to use quite frequently. Back when I was a young whippersnapper in my early twenties and living with my parents in a house with a crappy Internet connection, I used to fight endlessly with my family members over…
Continue Reading
More Articles →
My Projects:
These are ongoing projects that I’m working on, which I document in my blog.
Implementing a 2D game in QBASIC:
 |
Part 1: Graphics modes, drawing functions, and scan codesIn this episode, our hero discovers the wonders of the QBASIC language. Intrigued by its quirky capabilities, he learns the ropes in one night of feverish coding, as well as learning some neat tricks for getting the most out of the language. |
 |
Part 2: Functions, subroutines, and recursion, and more drawing functionsHere our hero explores functions and subroutines in the QBASIC language and starts getting into pixel-level drawing with the |
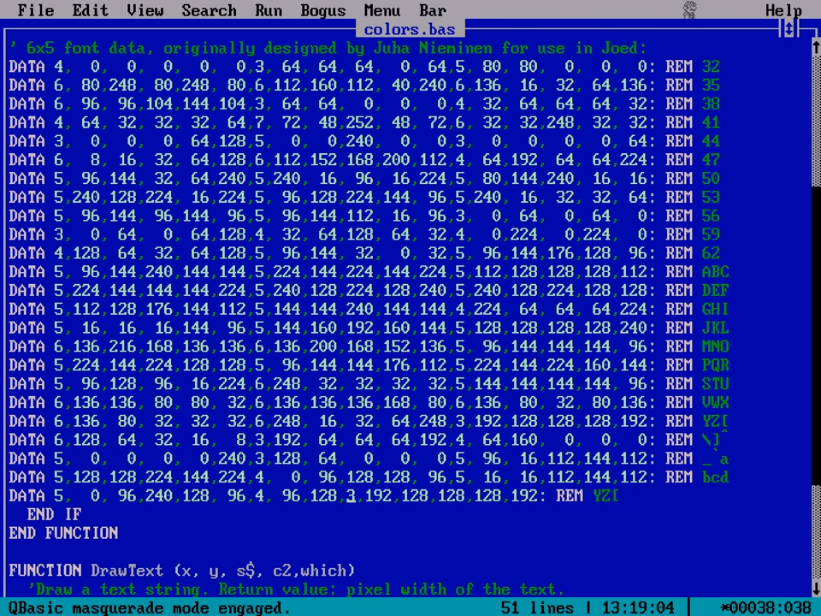
Part 3: Color tables, font files, and sprite animationHere our hero graduates to writing useful programs in QBASIC, starting with one that prints a color table. Not content to stop there, he then designs his own font, calling it PsychoFont 5×6, and creates a full-fledged sprite animation through iterative use of the |
My hacking arsenal, or, finding creative ways around tech lockdowns:
 |
Using Javascript and GIMP skillz to pirate fontsOur hero wants to use the Papyrus font for his art. Unfortunately it’s not on his computer and every download page for the font is paywalled. So he decides to be sneaky and write a script that will allow him to use the font for free. |
 |
Shell script to fuck with bandwidth throttling botsTake that, Ajit Pai! |
 |
Shell script to download photos directly from InstagramOur hero gets sick and tired of bullshit web interfaces interfering with his pastime of ogling sluts on the Internet and devises a plan to bypass Instagram’s default interface and get the boobies delivered directly to his hard drive. |
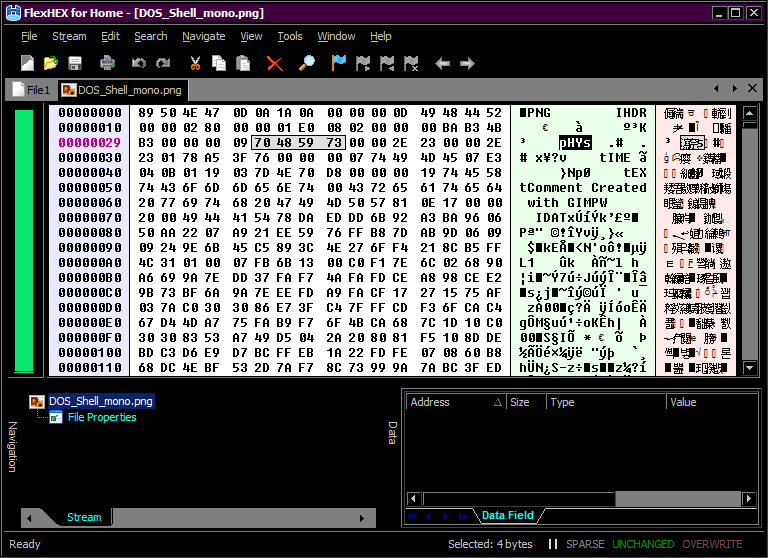 |
Hacking image filesOur hero gets into reverse engineering and starts digging through image files with a hex editor, trying to figure out how they’re built and how they can be safely altered without being corrupted or having their appearance changed. |
 |
Getting information on people the 1337 H4xx0r WayA mini-arsenal of tools and hacks for doing reconnaissance on people and organizations. |
Disassembling a Windows PE binary:
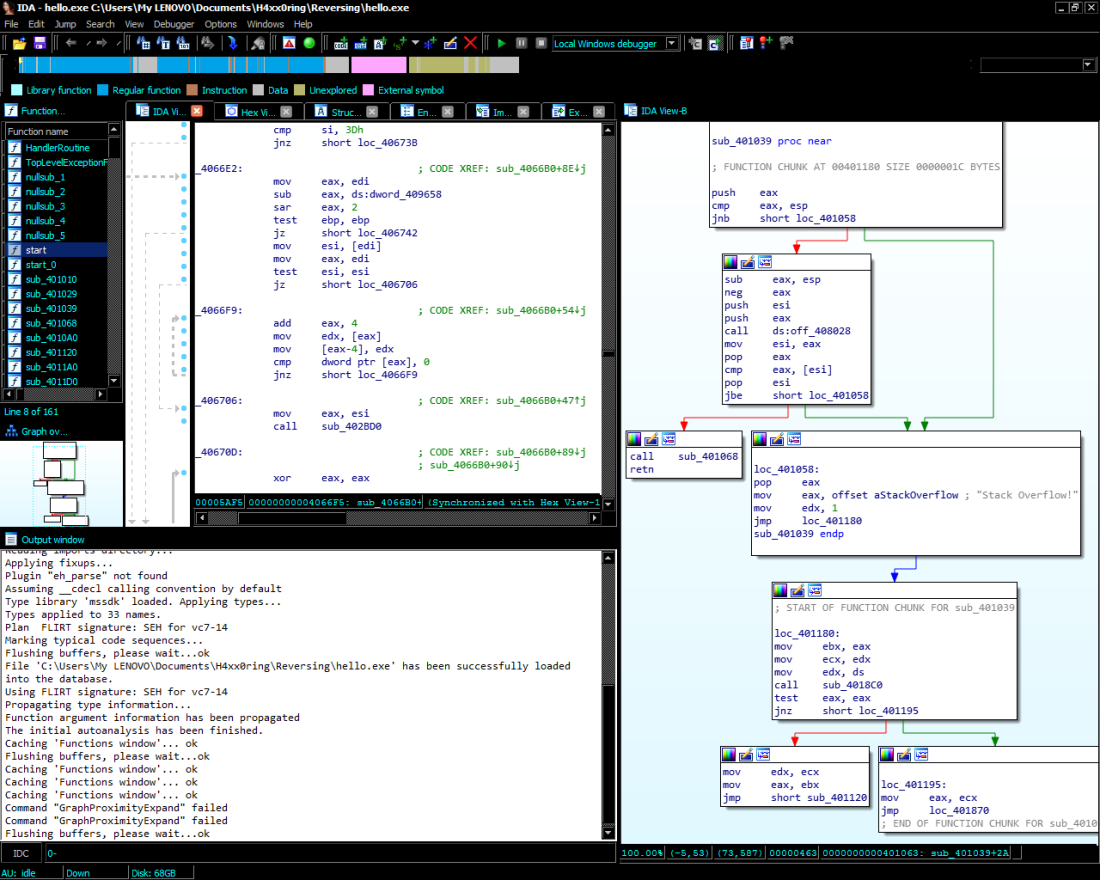 |
Introducing IDAOur hero starts using the IDA freeware disassembler to reverse-engineer Windows PE binaries, because he’s too cheap to actually pay for IDA Pro. |
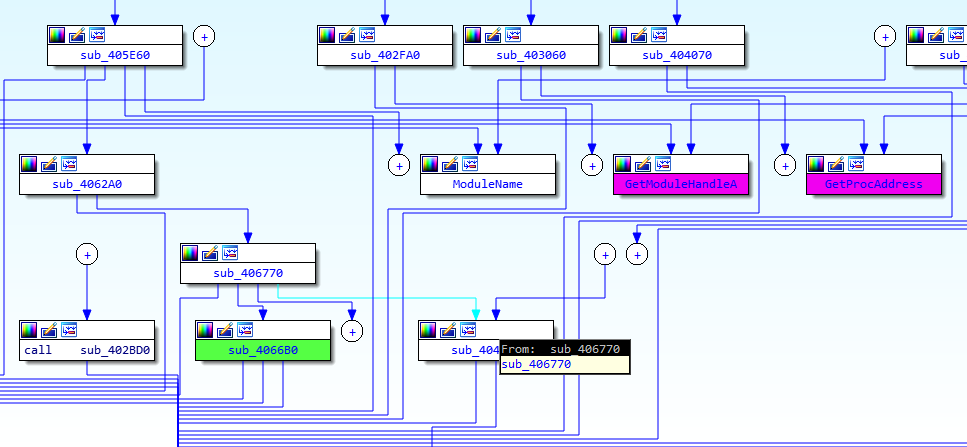 |
Deciphering the program setupNow that we’ve disassembled the binary, let’s start reading some assembly code! Everything up to the first WinAPI call is covered here. |
My Battlestation:
 |
Making the switch from Macbooks to ThinkpadsOur hero takes the essential first step in the construction of his battlestation and his hacker lair. It’s pretty hard to have an awesome hacker setup with a deliberately crippled hardware platform like the Mac. |
 |
Getting a new office chairAnother essential component. Can’t have an epic battlestation without something to put your butt on while you’re hacking. |
 |
The Ethernet IslandIn this chapter of our story, our hero builds an island of wired Ethernet connectivity inside the WiFi network imposed on him by his evil overlords (otherwise known as the tech staff), thus allowing him to control the security policy and other aspects of the system even though he’s not allowed to access the house’s gateway. |
 |
Escaping from the Matrix with the Van Eck tinfoil hatAfter suffering a psychotic episode, our hero becomes extremely paranoid about a government conspiracy against him. Here he envisions a completely isolated and unhackable air-gapped system that the Illuminati can’t get to. |
 |
Why Lenovo laptops are THE SHITOur hero reflects on why switching to Lenovo was probably the best decision he ever made in his career as a hacker. |
 |
The Tactical DOS VMOur hero works on some of the software for the rig – a super-secret DOS-based spy VM for doing spy stuff and h4xx0r stuff! |
 |
Using Arch Linux with the dual monitor setupOur hero hacks his system to run a text-mode Arch Linux system that utilizes both monitors. |
 |
Raspberry Pi RebootOur hero gives his Pi a complete makeover with a new OS, new software, and a new monitor, turning it into a complete Linux desktop and server. |
 |
My New Thinkpad X131eOur hero rambles excitedly about his new laptop. |
Corona-Chan Project: Predictive analytics for COVID-19:
 |
Part 1: Project launchOur hero wants to exploit the COVID-19 recession and buy cheap stocks that are guaranteed to go up when it’s over, but he wants to wait until the market hits its lowest point. So he devises a system to predict when the epidemic will hit its peak. Also made some predictions based on SARS which later turned out to be wrong. |
 |
Part 2: Smoothing the prediction functionOur hero modifies his data modeling program to smooth out the curve, because it’s all wonky and doesn’t make sense. |
 |
Part 3: Analyzing the prediction functionWe’re taking a step back from programming here to analyze the prediction function and how the smoothing of the curve distorts its critical points, research that will allow us to correct for such errors in the future. |
 |
Part 4: Fitting the model to the dataOur hero uses an empirical approach to find the critical points of the curve (meaning when the virus hits its peak). Later simplifications of the model have made much of this part of the research unnecessary, but it’s still interesting to look at. |
 |
Part 5: Final model-fitting programOur hero comes up with a more algebraic approach to the model-fitting problem and implements it with a program that performs logistic regression on the data, coming up with a ballpark estimate of when the peak of the virus will occur and how many confirmed cases there will be. |
MIX emulator:
 |
Project launchIntroducing the MIX emulator project… Our hero designs an emulator for the fictional MIX architecture used in Knuth’s famous TAOCP series. This introductory entry looks at the two main components of the system: an assembler for MIX assembly language code, and an execution environment for running MIX executables, both written in C. |
Highlight Reel:
Some of the best or most important articles I’ve written (in my opinion).
 |
Factorial OverflowWhile working on his latest coding masterpiece, our hero makes an astounding mathematical discovery. Read all about it here. |
 |
The Joy of HackingWhat does it mean to be a hacker? What does it mean to hack? What does the future hold for hackers and the hacker culture? All these and more questions are explored here. |
 |
Online Content Marketing and the Future of the EconomyFollow our hero’s journey in building his dreams and escaping from the rat race through the magic of passive income. Learn about his rules and secrets to success. |
 |
Adventures in VirtualBoxFollow the adventures of our intrepid explorer as he pushes the limits of retrocomputing with VirtualBox and travels to distant systems long forgotten by humanity. Explore the wonders of MS-DOS 6.22, Windows 2.0, Windows 3.1, OS/2 Warp, and Windows 95 in this whirlwind tour of computing’s past. |
 |
5 Things I Hate About Apple CultureListen to our hero rant about Apple-using hipsters and why their entire culture is fucking cancer. |
 |
5 Awesome Software Titles for DOSOur hero reviews some of his favorite DOS software on the market. Titles include After Dark, Borland Turbo C, Tandy Deskmate, DOS Navigator, and MATLAB. Tons of cool screenshots to look at in this article as well. |
 |
Marketable Skills (Random X11 Post)Oh shit, 15 years of knowing how to code and our hero still can’t get a job. Better stop procrastinating and learn some graphics programming so he can write programs that dumb normies can use. In this chapter our hero gets his feet wet with the X11 API and explains all the basic concepts so you guys can learn too. |
 |
Chickenshit Minimalism: How Apple Ruins Product Design for EveryoneOur hero makes the case that Apple’s shitty product designs are bad for everyone, not just Apple customers. |
Top Tutorials:
Learn how to do all kinds of neat stuff with computers.
 |
How Linux Package Managers WorkHave you ever wondered what goes on under the hood when you install a package in Linux? This tutorial will explain the exact step-by-step process, based on observations made while reverse-engineering |
 |
Custom Syntax Highlighting for VimLearn about our hero’s tried-and-true system for automatically adding custom syntax highlighting rules to Vim. |
 |
How to Write a Daemon Process in CEver wanted to write your own servers? Ever wondered what goes into making a Unix process run as a daemon so that it can provide services to other processes? This tutorial will explain the exact process, with example code so you can implement it yourself. |
 |
How to Block Websites and Prevent DNS Leaks Using Your Hosts FileThis tutorial will show you a quick-and-dirty method you can use to completely block any website, as well as to automatically access websites by their IP addresses to prevent DNS-related vulnerabilities when using a VPN. |
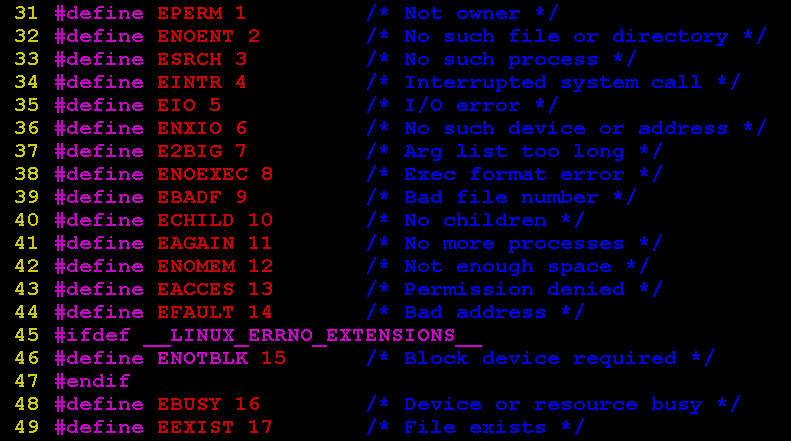 |
A Guide to Error Handling in CAll the information you will ever need to know about the C Standard Library’s error handling features, conveniently collected in one place. |
 |
How to Get the Dimensions of a Linux Terminal Window in CA tutorial that will come in handy for anyone wishing to implement full-screen terminal applications from the ground up. |
 |
Implementing the DoD Data Sanitation Algorithm in CExample code for how to implement DoD 5220.22 – the new state-of-the-art hard drive sanitation method designed to replace Gutmann. |
Odds and Ends:
Interesting nuggets that you probably won’t find anywhere else on the Web.
 |
Use SyncTERM as a Remote Login Terminal for the Raspberry PiThis tutorial will show you how to take two hitherto unrelated platforms and use one as a terminal for the other, just like in the old days of time-sharing networks. |
 |
Real Programmers Don’t Use StructsEver wondered how you would build complex data structures without using structs or objects? No? Well, I’m going to show you anyway, using the incredible power of void pointers! |
 |
How to Check the Byte Order (Endianness) of Your System in CThis tutorial will show you a quick method you can use to easily determine whether your CPU is little-endian or big-endian. |
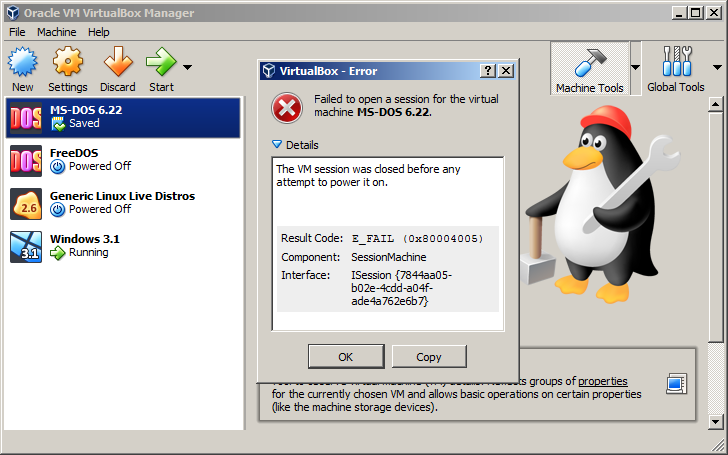 |
VirtualBox Data Recovery: How to Rescue Files from a Corrupted VMThis tutorial will give you some valuable tips in case you ever find yourself unable to start a VirtualBox VM because it’s corrupted and want to be able to access the files on that VM again. |
 |
Overcoming the Idiosyncrasies of C Programming in WindowsNot a lot is written about C programming on the Windows platform. This article looks at how C programming in Windows differs from C programming in Unix/Linux and how Windows C can be thought of as a subset of Unix C. |
All Other Articles (that aren’t utter shite):
 |
My top 5 favorite browser extensionsOur hero shares five browser extensions that are useful or just kinda cool. |
 |
Using Vim as a file browserLearn how to use the little-known file browsing capabilities of the Vim editor. |
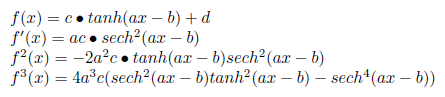 |
How to convert a TeX file directly to PDF formatAfter several frustrating attempts to make a PDF from a LaTeX file, our hero discovers a much simpler method that could have saved him a whole lot of time if he’d known earlier. |
 |
Up and Running: Using the TunnelBear VPN Service Through OpenVPNOur hero embarks on a fantastic journey towards ultimate privacy, in hopes of eventually wreaking havoc and anarchy on the world from behind his computer and not getting caught. Well, maybe. Can’t tell you too much right now, heheheh. |
 |
I’m not dead.Just so y’all know. |
 |
Forensics Tool to Detect Encrypted FilesRead about this fascinating digital forensics project that our hero started way back in May of this year and then never touched again. |
 |
Shared Memory ExploitsOur hero tries to actually git gud at hacking as opposed to just using stupid loopholes in software, starting with some research of the CVE database. |
 |
Run 64-Bit Guests in VirtualBox Using Hardware Virtualization (Lenovo Host)Ever gotten weird errors when trying to run 64-bit operating systems on VirtualBox VMs? This tutorial will explain what you need to do, using a Lenovo BIOS (though the knowledge found here applies to other hardware platforms as well). |
 |
How to Generate Truly Random Numbers in POSIX SystemsA tutorial on the generation of truly random numbers in C programs using the facilities of the POSIX system. |
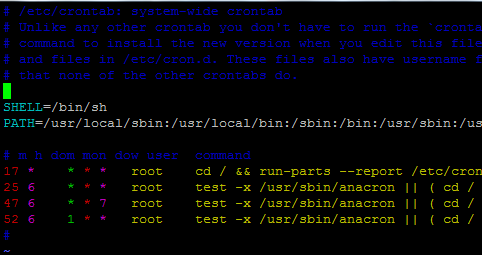 |
Scheduling Jobs in Linux with crontabLearn all about the legendary |
 |
The Michael Warren Free Software LicenseA software license designed by yours truly for the purpose of protecting open source software, its authors and contributers, and its users from those with malicious intent. |
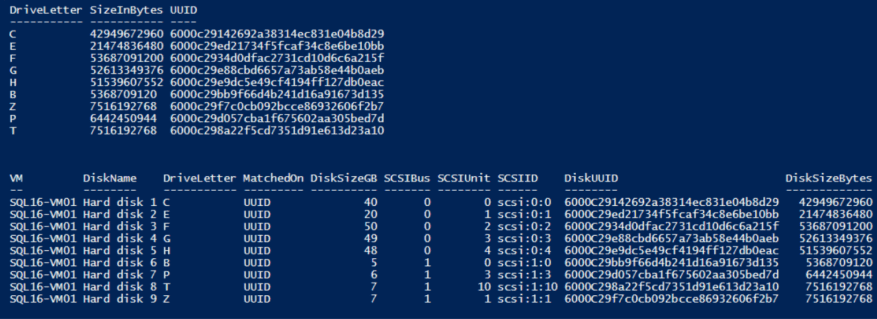 |
How to Generate UUIDs in LinuxLearn how to generate Universally Unique Identifiers from the Linux command line or in programs using the libuuid library. |
 |
The Lost Art of the All-NighterDo you like staying up late at night to work on coding projects? Does the midnight silence give you a buzz? Come here to have your love of nighttime hacking validated. |
 |
SSD Data Sanitation in LinuxLike the DoD article, but for SSDs. |
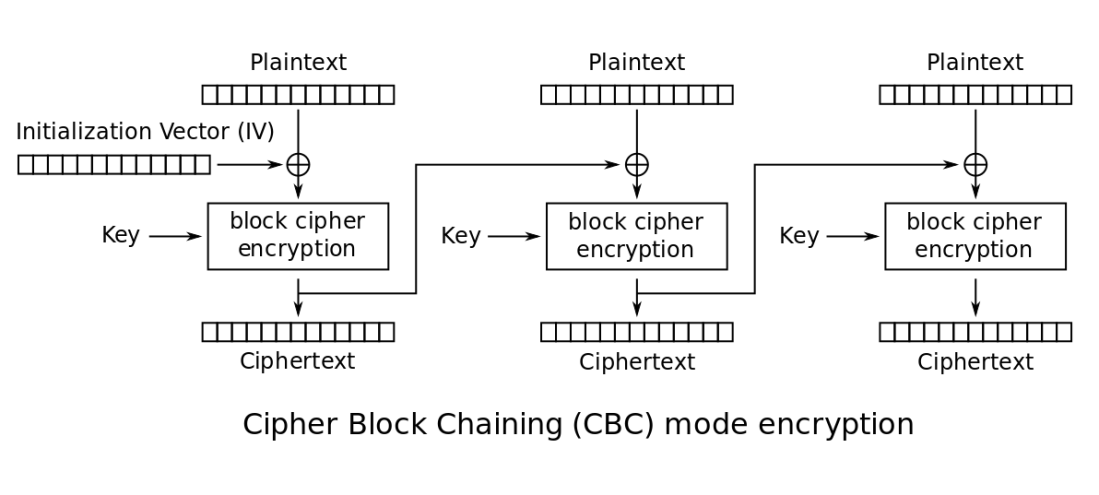 |
Understanding and Using the OpenSSL Command Line UtilityAn explanation of how to use the OpenSSL command line utility to encrypt and decrypt files, as well as some key concepts in cryptography theory. |
 |
Finding the Day Difference Between Two Dates in CJust some random C programming. |
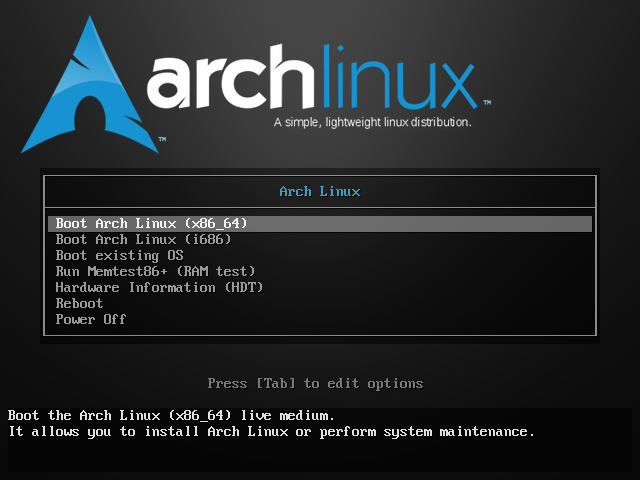 |
My Step-by-Step Process for Starting Arch Linux LiveOur hero details his exact sequence of steps for constructing a fully functional Arch Linux system from a minimalist live CD, because he can’t be assed to actually install anything. |
 |
Hi, Everyone!The first ever post on this site. Introducing our hero and his computing awesomeness. |